Protecting internal apps on Kubernetes with OAuth2 Proxy

Protecting internal apps with Github loginПодробнее

Kubernetes Dashboard Authentication using Keycloak OIDCПодробнее

Protect Your Apps: Managed SSO/OAuth Proxy (Google Cloud)Подробнее

Authenticating Proxy in Kubernetes: Simplified Guide with NGINX and OAuth 2.0Подробнее

OAuth2 Proxy: Secure Your Web App with Google Login (Easy!)Подробнее

k8s oauth2-proxy demoПодробнее

Leverage Single Sign-On with oauth2-proxy and IstioПодробнее

OAuth2 Proxy And NGINX integration with AZURE ADПодробнее

Kubernetes Security | Authenticating Webhook and Authentication Proxy ExplainedПодробнее

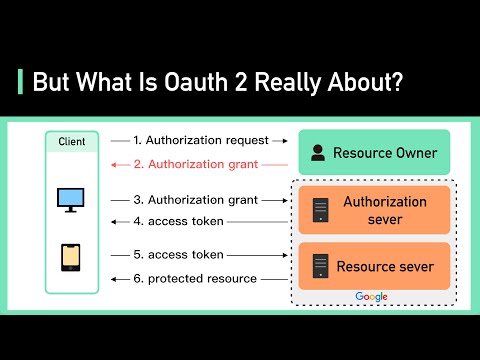
OAuth 2 Explained In Simple TermsПодробнее
Building Flux's Multi-Tenant API with K8s User Impersonation - Leigh Capili, VMwareПодробнее
Chappaai Update 01 (OAuth2 on Kubernetes Made Easy)Подробнее

Deploy Static Sites With Authentication For FreeПодробнее
Talk #1 Securing Kubernetes Service Using oauth2-proxy - Prasta Maha | #IOID21Подробнее

How to protect applications running in Kubernetes | Storware AcademyПодробнее

Topeaks #2 How to provision internal services and protect themПодробнее

Zipkin UI user validation with Oauth2 Proxy and KeycloakПодробнее

Browser Based Box with Oauth2-Proxy RestrictedПодробнее

Kubernetes Ingress Rule With Basic AuthenticationПодробнее
