picoCTF 2025 - Binary Exploitation - hash-only-1

Tutorial PicoCTF 2025 (158): Binary Exploitation: hash-only-1Подробнее

hash-only-2 - picoCTF 2025 - Binary ExploitationПодробнее

picoCTF 2025 - Binary Hacking - hash-only-1 - PATH HijackingПодробнее

Tutorial PicoCTF 2025 (159): Binary Exploitation: hash-only-2Подробнее

PicoCTF hash-only-1Подробнее

pico2025 hash-only-1Подробнее

Binary Exploitation vs. Web SecurityПодробнее

picoCTF 2025 - Binary Hacking - hash-only-2 - PATH Hijacking and Shell EscapeПодробнее

picoCTF 2025 - Binary Exploitation - Pie TimeПодробнее

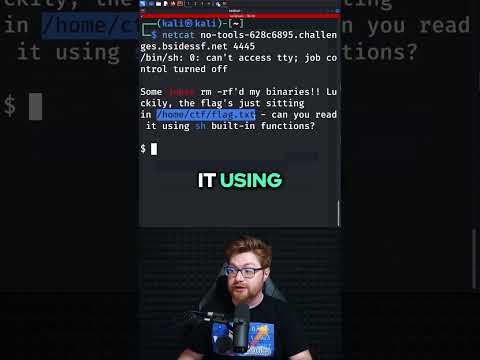
No Tools in a CTFПодробнее
picoCTF 2025 | n0s4n1ty 1 nosanity1Подробнее

PicoCTF 2025 - HashCrack Challenge | Cracking Weak Hashes WalkthroughПодробнее
