Permute Outputs - Applied Cryptography

Introduction to Cryptography: Substitution-Permutation NetworksПодробнее

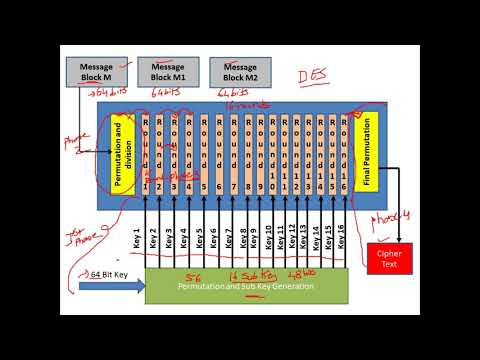
Data Encryption Standard (DES) - Explained with an Example - Cryptography - CyberSecurity - CSE4003Подробнее
Permute Outputs Solution - Applied CryptographyПодробнее

Block Cipher Standards (DES)Подробнее

Encrypt Outputs - Applied CryptographyПодробнее

Applied Cryptography: Internal Structure of DES - Part 1Подробнее

Encrypt Outputs Solution - Applied CryptographyПодробнее

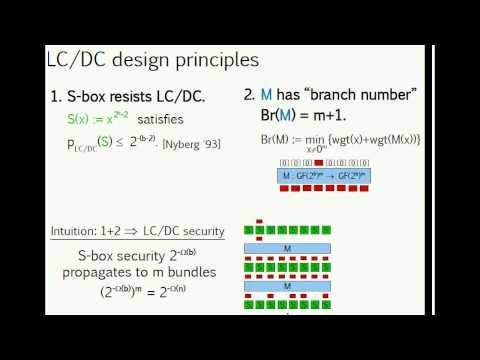
FSE 2018 - Farfalle: parallel permutation-based cryptographyПодробнее

Applied Cryptography: The Permutation CipherПодробнее

Beyond-Birthday-Bound Secure Cryptographic Permutations from Ideal Ciphers with Long KeysПодробнее

Applied Cryptography: Internal Structure of DES - Part 2Подробнее

Joan Daemen (STMicroelectronics & Radboud University) | Permutation Based CryptographyПодробнее

Putting It All Together - Applied CryptographyПодробнее

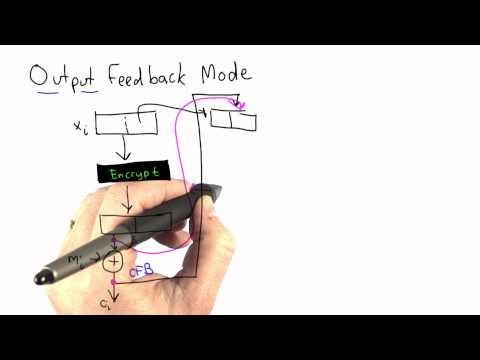
Output Feedback Mode - Applied CryptographyПодробнее
Decrpytion In Parallel - Applied CryptographyПодробнее

Substitution-Permutation Networks, Pseudorandom Function ...Подробнее
File Encryption Solution - Applied CryptographyПодробнее

Applied Cryptology 3.3: DES Block CipherПодробнее

Constructing a PRP (block cipher) from PRF using a Feistel networkПодробнее
