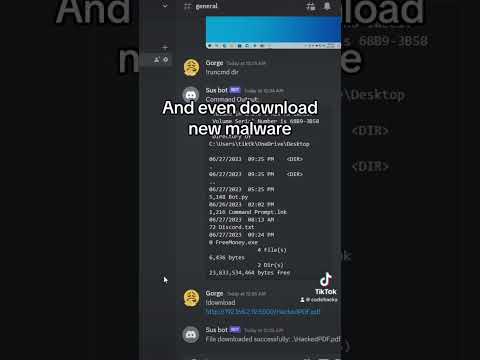
Never let this happen to you #hacker #hacking #coding #botnet #malware
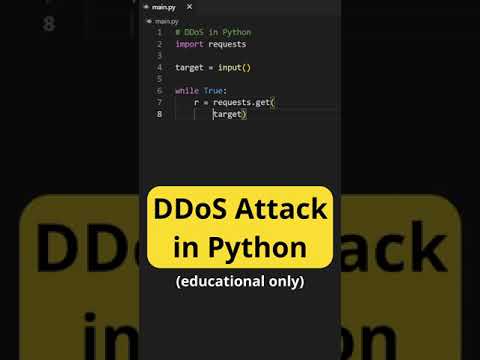
DDoS Attack in Python (educational purposes only)Подробнее
💾 HOW HACKERS CHANGE EVERY EXE FILE ⁉️ #hacking #tutorial #malware #virusПодробнее

🐍 UNDETECTABLE PYTHON VIRUS ❓😱 #shorts #Python #Security #malware #programmingПодробнее
DEF CON 18 - Dennis Brown - Resilient Botnet Command and Control with TorПодробнее
How to become a hacker in 1 minute? #hacker #ubuntu #hacking #linuxПодробнее
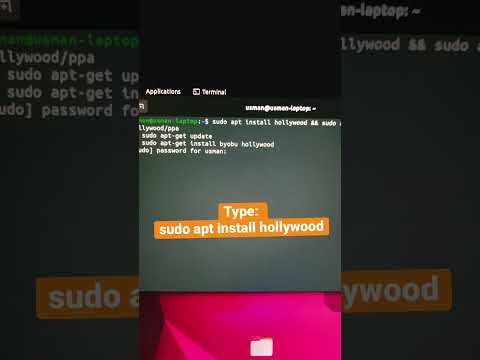
notepad hack #hacks #coding #code #linux #hacker #smartphone #cybersecurity #tech #trickywalaПодробнее
This Hacker Saved the InternetПодробнее

Remote Code Execution: Hacker's Holy Grail! #cybersecurity #hackers #ethicalhackingПодробнее

Hacking KnowledgeПодробнее

Hacker Shows How This USB Charger Can Hack Your Phonr In Seconds 🤯 #hacking #usarmy #shortsПодробнее

How botnets can turn you into a HACKER #shortsПодробнее

46% of hackers disseminating malware deliver it almost exclusively through email #cybersecurityПодробнее

You Weren’t Supposed to Learn Hacking Like This (13 Stories They Buried)Подробнее

3 SIGNS YOUR PHONE WAS HACKED!🤯Подробнее
How Botnets Work in Hacking #linux #botnet #hacking #cybersecurityПодробнее

How hackers can open hotel doors with a Flipper Zero @0dayCTFПодробнее

The Highest paid Ethical Hackers #ethicalhacking #cybersecurityПодробнее

Unlocking the Secrets of Cybersecurity: Inside the World of MDR and EDRПодробнее

Hard Hitting BotNetПодробнее

Hackers Use AI to Write Malicious CodeПодробнее
