Master Web Security with OWASP and OWASP Top Ten
🔒 Cybersecurity Class – OWASP Top 10 (No. 5): Security Misconfigurations | LIVE TrainingПодробнее

Complete Web Penetration Testing Exposed 🔥 (Beginner to Advanced) | burpsuite | Ethical HackingПодробнее

OWASP Top 10 Security Risks (Part 1) | CISSP Exam Guide | Web App Security ExplainedПодробнее

Master Cybersecurity & Software Development: OWASP Top 10 & Computational Thinking | TCBTПодробнее

Essential Web Security Best Practices GuideПодробнее

🔍 OWASP Top 10 – The Most Critical Web Vulnerabilities EXPOSED! 🔥Подробнее

become a master hacker with burpsuiteПодробнее

What Are the OWASP Top 10 Web Application Security Risks?Подробнее

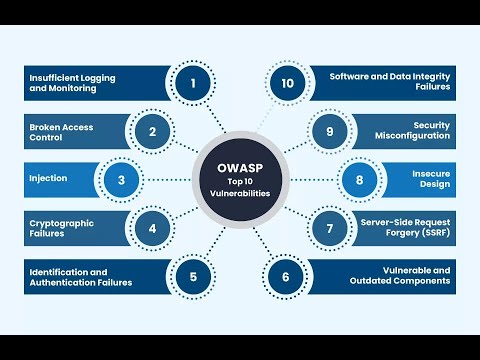
Master OWASP Top 10Подробнее

The ULTIMATE GUIDE to Master File Inclusion Vulnerability || Part - 1 || English SubtitleПодробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Cross-site Request Forgery (CSRF)Подробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Authentication - Final ChapterПодробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Authentication - Hard MediumПодробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Authentication - Level MediumПодробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Authentication - 2 #bugПодробнее

How to Master BugBounty: Broken Access Control | Owasp Top 10 | Authentication #bugПодробнее

How to Master BugBounty: Exploring Broken Access Control | Owasp Top 10 | Live Bug TestingПодробнее

How to Master BugBounty: Exploring Broken Access Control | Owasp Top 10 | Improper Access Control- 4Подробнее

How to Master BugBounty: Exploring Broken Access Control | Owasp Top 10 | Improper Access Control- 3Подробнее
