MAC Based on Hash Function | HMAC in network security
CNS : (unit-4) Criteria of hash algorithm || MDC || MAC || Types of MAC || BTech JNTUK/JNTUGVПодробнее

MAC vs. HMAC (einfach erklärt) | #CEHПодробнее

MAC (Message Authentication Code) | Unit 4 Cryptography and Cyber Security CB3491 | Anna UniversityПодробнее

HMAC (Hash Based Message Authentication Code) in Cryptography With Example #hmac #cns #jntuh #feedПодробнее

What is a Hashed Message Authentication Code (HMAC)?Подробнее

Message Authentication Code (MAC) | hash functionПодробнее

HMAC and CMAC in Cryptography Hash Function || Network Security in TeluguПодробнее

V4b: CBC-MAC and HMAC (Cryptography 101)Подробнее

Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in TeluguПодробнее

MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication CodesПодробнее

MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.Подробнее

4.2 Message Authentication, MAC, HMAC & CMACПодробнее

25-HMAC-Hashing Based Message Authentication CodeПодробнее

Protecting Data in Transit using HMAC and Diffie-Hellman in Node.jsПодробнее

H-MAC (Hash MAC) | Digaram and Concept | Information Security Tutorial by Nafay Ur RehmanПодробнее

CBC-MAC, CMAC, OMAC, and HMAC Message Authentication CodesПодробнее

7.6 MAC and HMACПодробнее

4.7 Hashed Message Authentication Code(HMAC) in TamilПодробнее

HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrityПодробнее
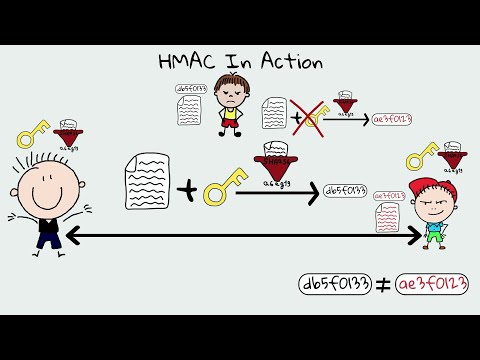
HMAC | Cryptography and Network SecurityПодробнее
