L13: Hashing Part 2 of 3 - Hash Functions

Basics of Cryptology – Part 13 (Modern Cryptography – Cryptographic Hash Functions)Подробнее

CS61B - Hashing 2 - Video 1 - Hash Table Recap, Default Hash FunctionПодробнее

Lecture 2. Hash Functions (Hash-Based Signatures)Подробнее

Hash Tables and Hash FunctionsПодробнее
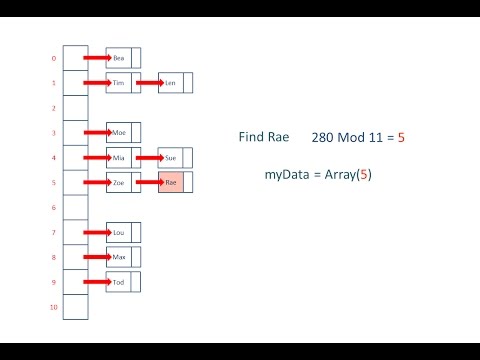
Applied Cryptography: Hash Functions - Part 2Подробнее

What is Hashing? Hashing Algorithm, Hash Collisions & Hash FunctionsПодробнее
Lecture 20: Hash Functions by Christof PaarПодробнее

Hash tables in 4 minutesПодробнее

🔴HASH CHURCH PART 2 ⛪️Подробнее

137 Extendible Hashing (Dynamic Hashing) - Numerical ExampleПодробнее

Hashes 2 Hash FunctionsПодробнее

Lecture 1.2 - Cryptographic Hash Functions part 2Подробнее

W2022 CS 210 Lecture 14 (Hashing, Hash Function, Hash Codes)Подробнее

Hash Tables (part 2): Resolving CollisionsПодробнее

What is a Hash Table? | Separate ChainingПодробнее
2-Hash Function in HashingПодробнее

How Password Hashing Works: Keep Your Data SafeПодробнее

Hashing 2: Making a hash functionПодробнее

Day 30: Hashing Algorithms for Passwords | #CybersecurityAwarenessMonth 2023Подробнее
