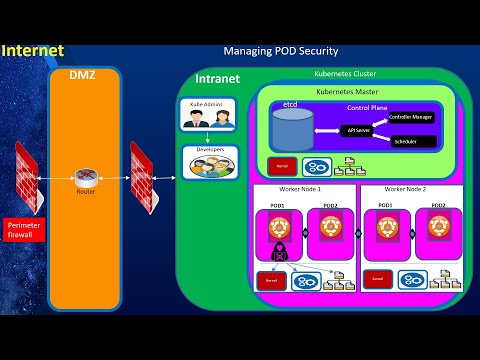
Kubernetes Security, Part 1: Kubernetes Security Overview and Role Based Access Control (RBAC)
Part 1 | Elastic Kubernetes Service Architecture | Deep Dive into Internals for Top 10 EKS SecurityПодробнее

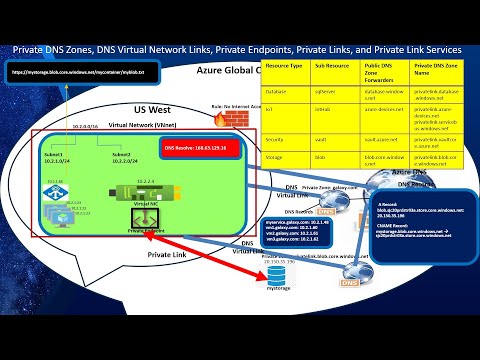
Azure Networking Series: Part 3, Private DNS Zone, Private Link/Endpoints, and Private Link ServicesПодробнее
AZ-500: Plan and Implement Advanced Security for Compute - Part 1Подробнее

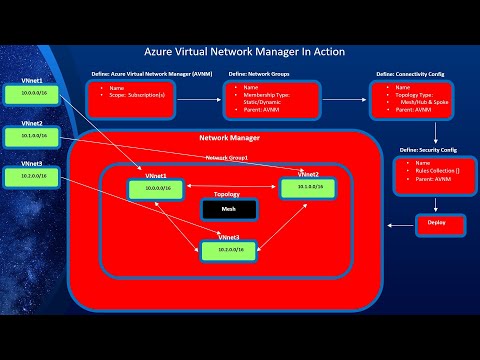
Azure Networking Series: Part 2, Azure Network TopologiesПодробнее
Azure Networking Series: Part 1, IntroПодробнее
26. 🔒Master Kubernetes RBAC PART-2 : Secure Your Cluster with Real-World Examples🔒Подробнее
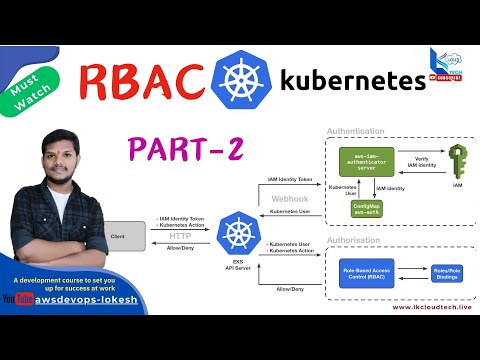
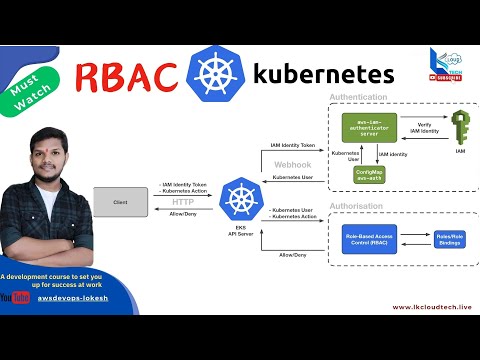
25. Master Kubernetes RBAC PART-1 : Secure Your Cluster with Real-World ExamplesПодробнее
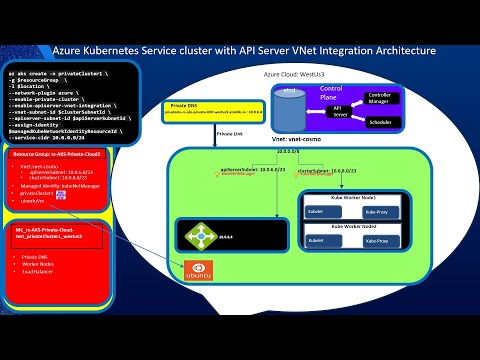
Setup Azure Kubernetes Private Clusters with API Server Vnet IntegrationПодробнее
Mastering AWS EKS Kubernetes DevOps Project | Intro | Part 1Подробнее

Workload Identity Part 2: How Cilium Implements Its Mutual Auth Leveraging SPIFFE and SPIREПодробнее
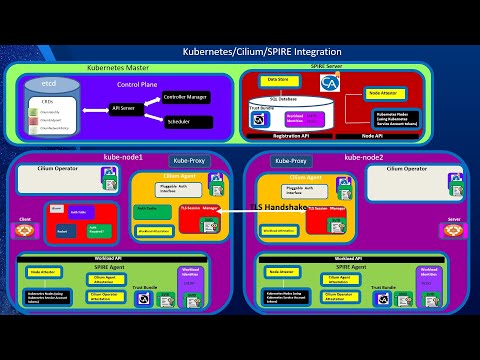
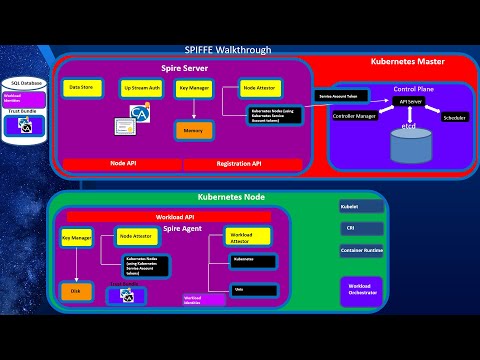
Workload Identity Part 1: Introduction to SPIFFE and SPIREПодробнее
Part 1 Common Security Hurdles in Kubernetes & Active Directory | Eric Kuehn & Cory SabolПодробнее

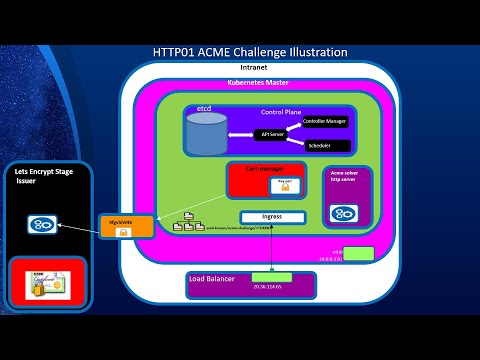
Encrypt Client Communication to Kubernetes Services Leveraging Cert-Manage and Let’s EncryptПодробнее
What is RBAC | Why RBAC is Important | Newly enabled features of RBACПодробнее

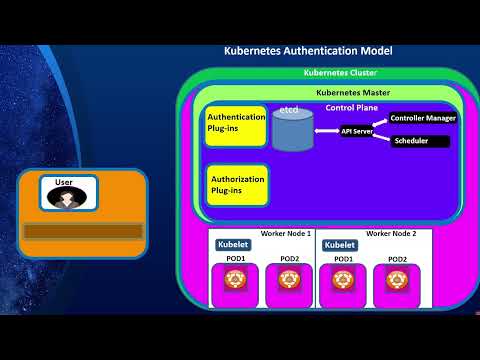
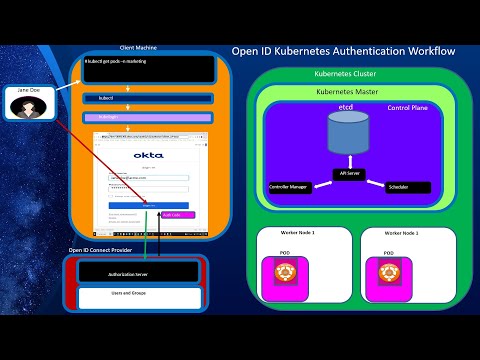
Kubernetes Security, Part 4: Kubernetes Authentication (Part B: Open ID Connect Auth)Подробнее
🦝 RBAC to the Future: Untangling Authorization in Kubernetes - Jimmy Mesta, KSOCПодробнее

Kubernetes Security, Part 3: Kubernetes Auth (Part A: Overview and X509 Client Certificate auth)Подробнее
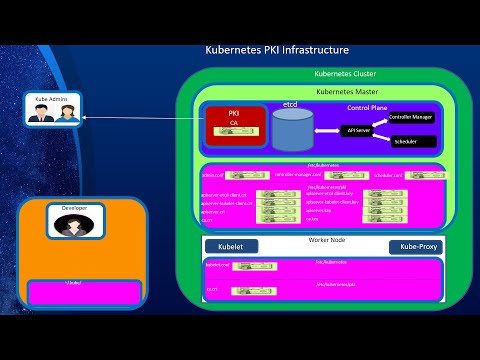
Introduction to Kubernetes Security - Marc BoorshteinПодробнее

Kubernetes Security, Part 2: Managing POD Run Time SecurityПодробнее