JWT Security Vulnerabilities | CyberSecurityTv

Exploiting and Fixing Client-Side Path Traversal (CSPT) Vulnerabilities | CyberSecurityTVПодробнее

JWT Explained in Depth | CyberSecurityTvПодробнее

What are OAuth Security Vulnerabilities | CybersecurityTvПодробнее

what is jwt token authentication | attacking jwt for beginnersПодробнее

The Hacker's Guide to JWT SecurityПодробнее

The Hacker’s Guide to JWT Security by Patrycja WegrzynowiczПодробнее

Why is JWT popular?Подробнее
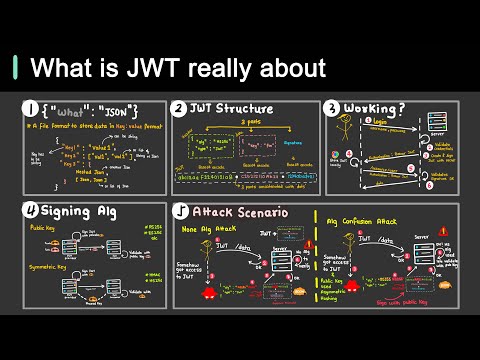
How JWT token works ?Подробнее
Introduction to JWT AttacksПодробнее

The Hacker's Guide to JWT Security - Patrycja WegrzynowiczПодробнее

The Hacker’s Guide to JWT Security, Patrycja WegrzynowiczПодробнее

Hands-On Realistic Pentesting - How to Exploit JWT VulnerabilitiesПодробнее

6 JWT Tips!Подробнее

JWT as session token || How JWT is used to manage HTTP session?Подробнее
Are You Properly Using JWTs? - Dmitry SotnikovПодробнее

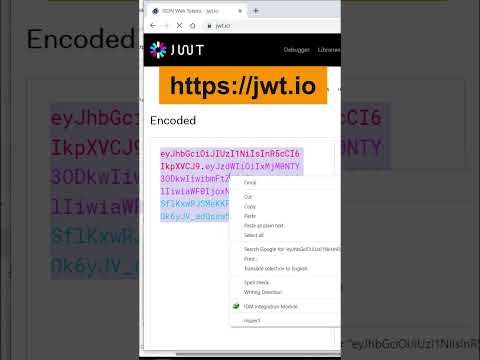
How to see content of a JWT ( Json Web Token ) ?Подробнее
Understanding and Avoiding JWT Weak Signing Keys Vulnerabilities: Complete TutorialПодробнее

The Hacker's Guide to JWT Security by Patrycja WegrzynowiczПодробнее

Cracking JWTs | Web Security AcademyПодробнее
