java sha256 hash with salt example

Hash vs Salted Hash (How to store password) JavaПодробнее

Java - Simple setup for hashing algorithms: MD5, SHA-1 and SHA-265.Подробнее
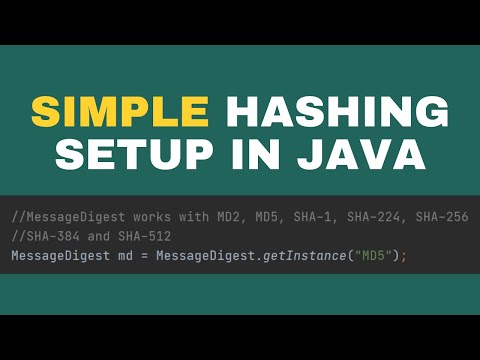
SHA256 javaПодробнее
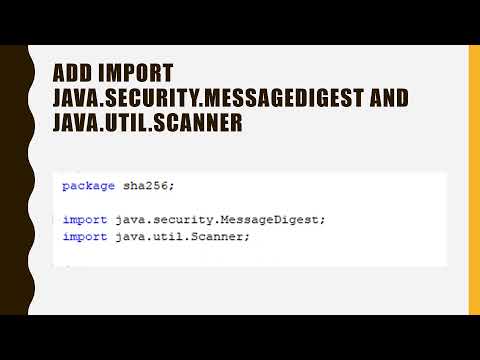
SHA256 Hashing online Using Java -springBoot online CalculatorПодробнее
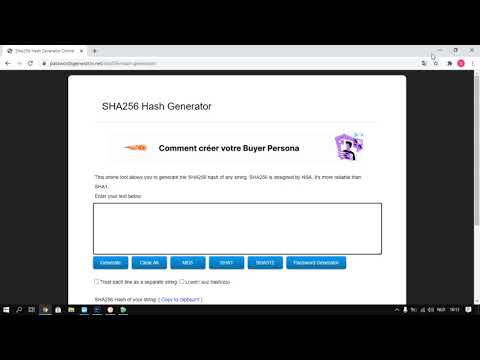
Password Hashing, Salts, Peppers | Explained!Подробнее

java sha256 exampleПодробнее

What Is A Hash Function How SHA256 Works In Blockchain Cryptography Used Hashing Algorithm ExplainedПодробнее

Secure OTP Verification | Hashing Technique | Java #java #coding #programming #hashing #sha256 #otpПодробнее

sha 256 string in javaПодробнее

How to Encrypt and Decrypt Passwords in Java Using SHA-256Подробнее

SHA256 Hash in JavaПодробнее

java sha256 implementationПодробнее

HASH Functions: SHA-512, SHA-256, SHA-1, MD5 (JAVA)Подробнее

Java Bcrypt example - salt + pepperПодробнее

SHA-256 Encryption and Decryption in Java: ExampleПодробнее

Java :How to hash some String with SHA-256 in Java?(5solution)Подробнее

Java Tutorial - Hash functions (MD2, MD5, SHA-1, SHA-224, SHA-256, SHA-384, SHA-512)Подробнее

How to crack sha256 hash using JohnПодробнее

SHA-256 | COMPLETE Step-By-Step Explanation (W/ Example)Подробнее
