Introduction to Threat Modeling Diagrams SHORT

IriusRisk Threat Modeling Tool: An overview in under 3 minutesПодробнее

What Is an Attack Graph? #shortsПодробнее

Threat modelling with OWASP Threat DragonПодробнее

STRIDE Threat Modeling for Beginners - In 20 MinutesПодробнее

Introduction to Threat Modeling: Understanding the BasicsПодробнее

Introduction to Threat Modeling Diagrams in Enterprise ArchitectПодробнее

What is Threat Modeling and Why Is It Important?Подробнее

Understanding STRIDE: An Easy Guide to Threat ModelingПодробнее

Data Flow diagrams in Threat ModelingПодробнее

Beginners Threat ModelingПодробнее

Create Threat Model Diagram OnlineПодробнее

Introduction to Threat Modeling by Avi Douglen - 11 JunПодробнее

A New Approach to Threat ModelingПодробнее

Use STRIDE To Do A Quick Threat Modeling On A Simple Web Application (Step by Step Guide)Подробнее
Threat Modeling Explained| How to implement threat modeling| Pros and Cons of Threat Modeling MethodПодробнее
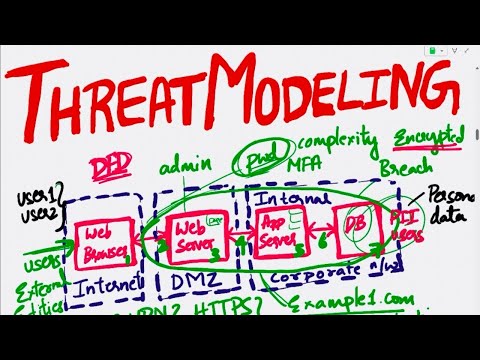
Threat Modeling Frameworks for Information Security Analysts | Threats and Attack VectorsПодробнее

What is Threat Modeling Methodologies, Types, and Steps | What Is Threat ModelingПодробнее

How to do Real World Threat ModelingПодробнее
What Is A Data Flow Diagram In Threat Modeling? - SecurityFirstCorp.comПодробнее

STRIDE Threat Modeling using Microsoft Threat Modeling ToolПодробнее
Threat Modeling in less than a minute #shortsПодробнее

1. Introduction, Threat ModelsПодробнее

Artur Balsam - Threat Modelling 101 - Ory Summit 2022Подробнее