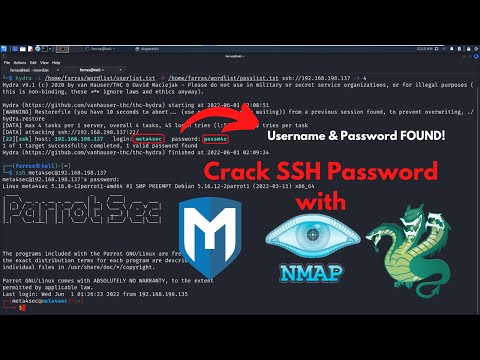
Intro to Metasploit: SSH Brute Force Attack

SSH Brute-Force Attack with Metasploit & Nmap (Step-by-Step) | VMware Series Ep. 7Подробнее

Brute force SSH attack | Ethical Hacking Tutorial(2025) #SSH#BruteForce#EthicalHacking#CyberSecurityПодробнее

Brute Force on ssh using Hydra and metasploitПодробнее

HACKERS Exposed: Brute Forcing SSH Logins with Metasploit on Kali LinuxПодробнее

Brute force attack on ssh using metasploitable gone wrong😢 - 30Days learning-to-hack Challenge Day20Подробнее

Exploit SSH via Brute Force || YT Short #securityvulnerability #coding #metasploitframeworkПодробнее

Exploiting SSH via Brute Force on Metasploitable 2 Using Hydra & MetasploitПодробнее

How To Brute Force SSH Using Metasploit Framework Ethical Hacking Tutorial MalayalamПодробнее

Ethical Hacking - SSH Brute ForceПодробнее

اختراق الاجهزه والسيرفرات عن طريق ssh brute force attack : كورس metasploitПодробнее

SSH brute force Penetration test on metasploitable 2 شرحПодробнее

SSH Bruteforce Pakai Hydra & MetasploitПодробнее

Belajar Dasar Ethical Hacking Lengkap Part 25 SSH Bruteforce Attack dengan Crunch & MetasploitПодробнее

MetaSploit SSH Bruteforce | MetaSploit on TermuxПодробнее

Metasploit TutorialПодробнее

Brute Forcing SSH with MetasploitПодробнее

Learning Hacking with metasploitable - 3 Attack Brute Force SSH with MetasploitПодробнее

Hack Linux, Windows System/Server (Brute Force ssh) with Metasploit | CEH v12 TutorialПодробнее
SSH Brute Force with Hydra, Nmap, and Metasploit Comparison | Security AwarenessПодробнее