Intro to asymmetric public key cryptography rsa encryption
RSA Cryptography Song (Asymmetric-key Algorithms) (Public-key Encryption)Подробнее

Introduction to Asymmetric Cryptography - Euler's Theorem & RSA ProofПодробнее
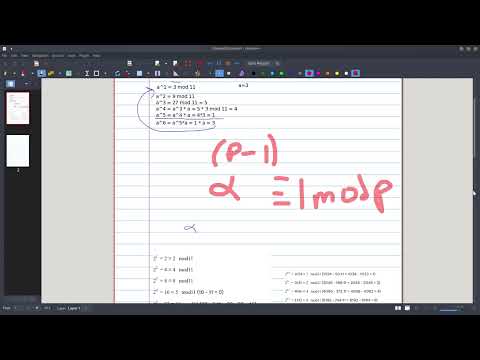
RSA Cryptosystem ||Asymmetric Cryptosystem || Public Key Cryptography || Cryptography & Network SecПодробнее

Cryptography and Network Security-Introduction▶️Makaut CSE IT 8th sem #makaut #crypto #network #aiПодробнее

CySec101 / EP.22 / Public Key Cryptography Intro / TryHackMe Cyber Security For BeginnersПодробнее

Introduction to Encryption & Cryptography Secure Communication Full Course No ConfigLAB 2hrПодробнее

Public Key Cryptography Basics | Cybersecurity 101 Learning Path - TryHackMeПодробнее

RSA Algorithm in Tamil | Cryptography and Cyber Security in Tamil | CB3491 Lectures in Tamil Unit 4Подробнее

Elliptic Curve Cryptography in less than 5 minutesПодробнее

V7c: RSA encryption (Cryptography 101)Подробнее

RSA Key Exchange and Forward Secrecy - Cryptography EssentialsПодробнее

The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.Подробнее
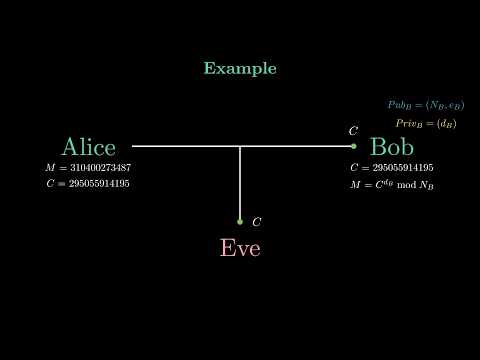
Cryptography Asymmetric Public key Cryptography RSA algorithmПодробнее

RSA & Asymmetric Encryption - Cryptography EssentialsПодробнее

Introduction to Asymmetric Key Cryptography || Lesson 56 || Cryptography || Learning Monkey ||Подробнее

RSA algorithm in cryptography and Network Security || Asymmetric techniquesПодробнее

Asymmetric Encryption Using RSA (Private & Public Key) in Spring BootПодробнее

Cryptography Essentials - Series IntroПодробнее

From substitutions to public keys - an introduction to cryptographyПодробнее

INTRODUCTION OF ASYMMETRIC KEY CRYPTOGRAPHY WITH EXAMPLE (BANGLA)Подробнее
