Integer Overflow vulnerability prevention explained

The State of Kernel Self-ProtectionПодробнее

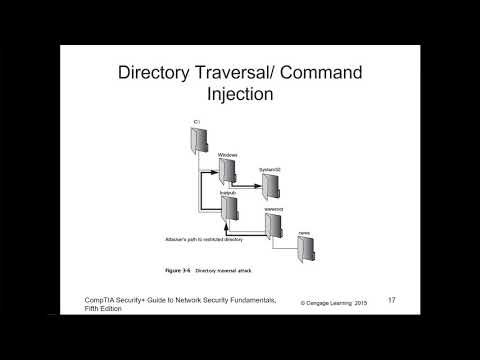
CompTIA Security+ - Chapter 03 - Application and Networking Based AttacksПодробнее
What is an Integer Overflow Vulnerability? | Hacking 101Подробнее

CSE 523S - Integer Overflow Vulnerability in Simple termsПодробнее

Buffer OverflowПодробнее

Running a Buffer Overflow Attack - ComputerphileПодробнее
Integer/ Buffer Overflow Vulnerability - Real World ExampleПодробнее
#22 Integer Vulnerabilities | Information Security 5 Secure Systems EngineeringПодробнее

Secure by Design: C++ (Integer Overflow)Подробнее

PHP INTEGER UNDERFLOW/OVERFLOW VULNERABILITYПодробнее

how do hackers exploit buffers that are too small?Подробнее

Lecture 3 - Integer OverflowПодробнее

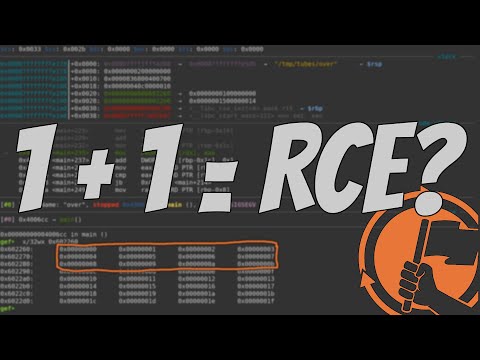
When Integer Overflows attack: How an Integer Overflow can can lead to Remote Code ExecutionПодробнее
Software Security: Vulnerabilities - Integer/Buffer OverflowПодробнее

060 Integer Overflow AttacksПодробнее

Integer Overflow Vs. Integer Underflow? - Tactical Warfare ExpertsПодробнее

Demonstrating an Integer Overflow in Bitdefender Internet SecurityПодробнее

#7 - 35C3 Junior CTF 2018 "Arraymaster" - From Integer Overflow to ShellПодробнее

Integer overflow and underflow explainedПодробнее

Integer Overflow Attack Exploit | Turning $200 to $1943133260 | Infosec | Binary ExploitationПодробнее

Integer Overflow AttackПодробнее
