ICS/OT Secure Remote Access
How Do Attackers Hack into ICS/OT Networks?Подробнее

ICS Vulnerability Report: Insights, Trends and Predictions for OT Cybersecurity in 2025 | VerveПодробнее

Recorded Webinar | HERA – Hardware-Enforced Remote Access | Secure Remote Access for OTПодробнее

Webinar | HERA – Hardware-Enforced Remote Access | Secure Remote Access for OTПодробнее

Webinar | HERA – Hardware-Enforced Remote Access | Secure Remote Access for OTПодробнее

HERA - Hardware Enforced Remote Access for OT Environments | Secure Remote Access for ICSПодробнее

2023 ICS/OT Cyber Security Survey: Adapting to New ThreatsПодробнее

Zero Trust Access Management & Remote Access for OT-IT-CloudПодробнее

IAM Solutions: Secure Access in ICS & Cyber-Physical SystemsПодробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 11 (Review Questions)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 10 (Intro to ICS/OT Penetration Testing)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 9 (Industry Standards & Regulations)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 8 (Incident Detection & Response)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 7 (OSINT for Industrial Control Systems)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 4 (Secure Network Architecture)Подробнее

Ron Fabela: Secure Access That Makes Sense for OperationsПодробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 3 (Control Systems & Protocols)Подробнее

Getting Started in ICS/OT Cyber Security - 20+ Hours - Part 2 (ICS/OT Cyber Security Overview)Подробнее

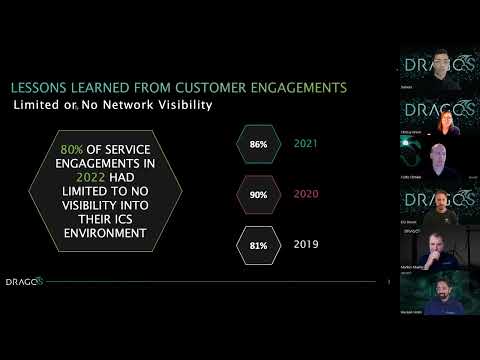
Webinar | 2022 ICS/OT Cybersecurity Year in Review - Lessons Learned from the FrontlinesПодробнее
OT Secure Remote Access How to Benefit from Zero Trust Network Access in Industrial SettingsПодробнее
