HTTP tunneling with Tunna v1.1a using proxychains

SSH tunneling with ProxychainsПодробнее

Linux SSH Tunneling With ProxychainsПодробнее

Don't get caught! Hide Yourself w/ Proxychains and TORПодробнее

Proxychains! - Proxy Series #1Подробнее

Proxychains and TunnelingПодробнее

Hak5 - SSH Tunneling with Proxychains, Hak5 1119 part3Подробнее

How can I tunnel all of my network traffic through SSH?Подробнее

Hak5 - SSH Tunneling with Proxychains, Hak5 1119 part2Подробнее

How HTTP Tunneling works, The CONNECT method, Pros & Cons and moreПодробнее

Hak5 - SSH Tunneling with Proxychains, Hak5 1119 part1Подробнее

Anonymizing Linux Traffic with ProxyChains & Tor – Step-by-Step Guide!Подробнее

TekTip ep10 - ProxychainsПодробнее

How to Make an SSH Proxy TunnelПодробнее

Pivoting Using SSH Tunneling & Proxychains || 2021 || LalithKumarПодробнее

SSH Tunneling , SOCKS and Pivoting with ProxyChainsПодробнее

pivoting [step 3 hard level] SSH tunneling Dinamically Reverse and proxychainsПодробнее
![pivoting [step 3 hard level] SSH tunneling Dinamically Reverse and proxychains](https://img.youtube.com/vi/hN9L9LLDMc8/0.jpg)
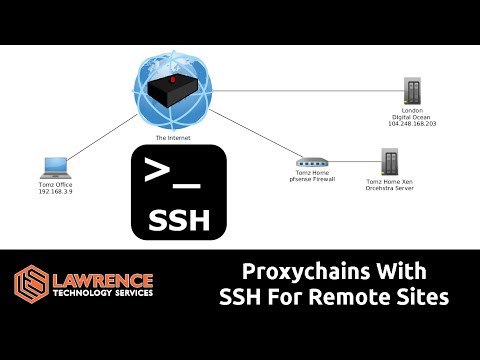
Linux Proxychains Using SSH & SOCKS Proxy For Easy Remote Management & TestingПодробнее
CYPHERCON13 14 Hypervault Demo and HTTP and SSH Tunneling Caleb MadrigalПодробнее

How VPNs use tunneling and encryptionПодробнее
