How to Find the Address of a String in Binary Using gdb

Temple Of Pwn - Part 2: Format StringsПодробнее

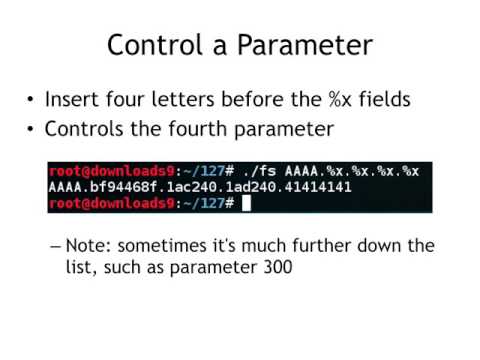
CNIT 127 Ch 4: Introduction to format string bugsПодробнее
Reverse Engineering with Binary Ninja and gdb a key checking algorithm - TUMCTF 2016 Zwiebel part 1Подробнее

Finding main() in Stripped Binary - bin 0x2CПодробнее

GDB is REALLY easy! Find Bugs in Your Code with Only A Few CommandsПодробнее
Reverse Engineering BinariesПодробнее

How to Print the Full Value of a Long String in GDBПодробнее

How to search for a byte sequence in memory with GDB command find?Подробнее

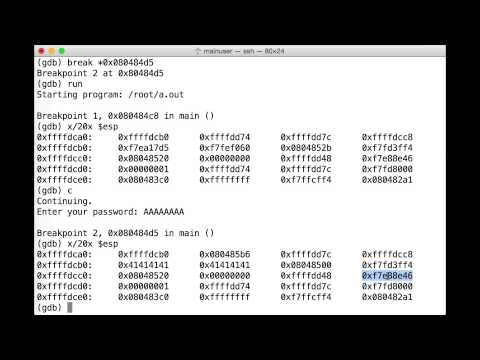
Finding Buffer Overflow Offsets in GDBПодробнее

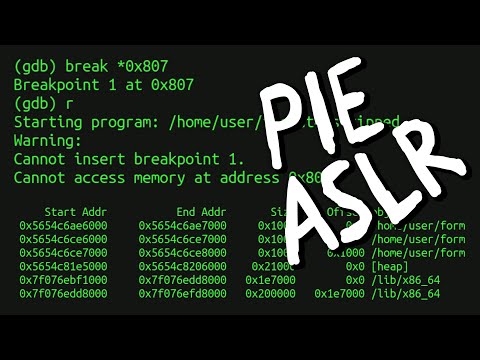
Cannot access memory at address // Debugging PIE Binaries affected by ASLR - bin 0x2EПодробнее
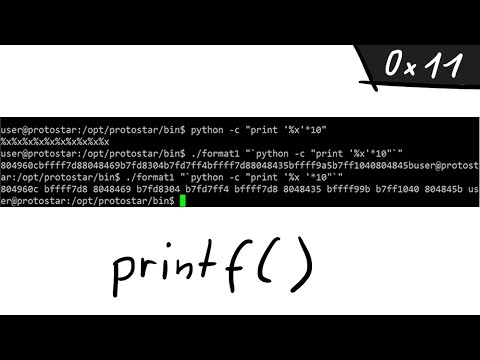
A simple Format String exploit example - bin 0x11Подробнее
Debugging and Disassembling our Simple C Program Binary Artifact using the GDBПодробнее

How They Hack: Buffer Overflow & GDB Analysis - James LyneПодробнее
Buffer Overflows with GDB and GEFПодробнее
Using #Linux #Commands analyze Unknown Binary | #strings, Avast's #retdec, #ltrace, #strace, #gdbПодробнее

Reverse Engineering w/GDB and Ghidra! | picoCTF 2022 #08 "Keygenme"Подробнее

Debugging a Stripped Binary in GDB! - picoCTF "not crypto" challengeПодробнее

2020 05 01 : Linux: gdb - disassembleПодробнее

vfprintf internal buffer - Advanced Format String (part 1) - Binary Exploitation PWN101Подробнее
06 - Program Segments and Debugging with GDBПодробнее

Radare2 Series 0x3 - Debugging Part 1 Runtime Analysis and Binary PatchingПодробнее
