How Does SSH Encryption Work? - Your Computer Companion

What Is X11 Forwarding? - Your Computer CompanionПодробнее

How To Use SSH Config File For RDP Tunneling? - Your Computer CompanionПодробнее

How SSH WorksПодробнее

How SSH Really WorksПодробнее

Public Vs Private Keys In SSH? - Your Computer CompanionПодробнее

SSH KeysПодробнее

SSH explained in 2 minutes!Подробнее

How Secure Shell Works (SSH) - ComputerphileПодробнее
How does SSH encryption work?Подробнее

How SSH WorksПодробнее

SSH Keys: What They Are and How They WorkПодробнее

9 - Cryptography Basics - SSH Protocol ExplainedПодробнее
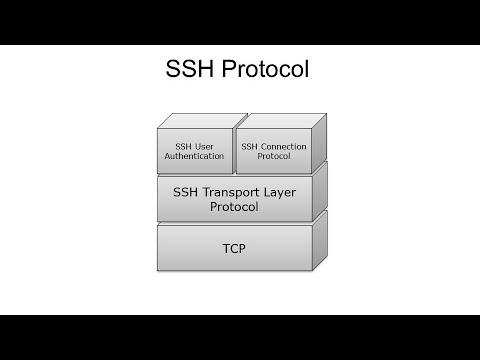
SSH ExplainedПодробнее

How SSH WorksПодробнее

SSH Encryption, Authentication, and Message Authentication | SSHПодробнее

How SSH password-less key based authentication work in 4 minutes (with example)Подробнее

the basics of secure shell (ssh)Подробнее

Day 30: How HTTPS & SSH Work | What is Encryption? | Symmetric & Asymmetric Encryption | CKA 2025Подробнее

Encryption EXPLAINED in 30 seconds👩💻 #technology #programming #software #tech #computerscienceПодробнее

How does encryption work?Подробнее
