#features #smart Hash-based Message Authentication Code (HMAC)

MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication CodesПодробнее

HMAC explained | keyed hash message authentication codeПодробнее

Hash Based Message AuthenticationПодробнее

#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|Подробнее

[HMAC] - Hash Based Message Authentication CodeПодробнее
![[HMAC] - Hash Based Message Authentication Code](https://img.youtube.com/vi/g7Uvr2izN5k/0.jpg)
25-HMAC-Hashing Based Message Authentication CodeПодробнее

Hash based Message Authentication Code (HMAC)Подробнее

What is HMAC, Hashed message authentication codeПодробнее

Securing Stream Ciphers (HMAC) - ComputerphileПодробнее

HMAC - Hash-based Message Authentication CodeПодробнее

Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - CryptographyПодробнее

What is an HMAC? | Hash-Based Message Authentication Code | Online Hmac Generator ToolПодробнее

MAC Based on Hash Function | HMAC in network securityПодробнее

What Is HMAC (Hash-based Message Authentication Code)? - SecurityFirstCorp.comПодробнее

HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrityПодробнее
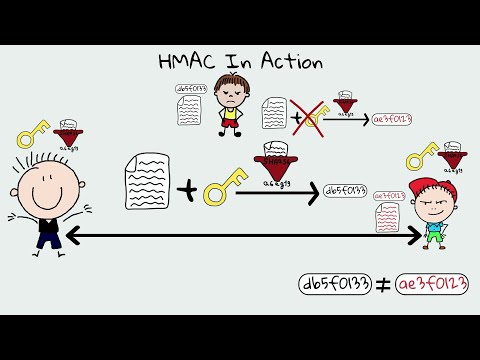
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network SecurityПодробнее

Lecture 22: MAC (Message Authentication Codes) and HMAC by Christof PaarПодробнее
💥 JWT HS256 Signature - Learn What is a Hash-Based Message Authentication Code (HMAC)Подробнее

Hashed Message Authentication Code HMACПодробнее
