Exploitation and Buffer Overflows with Narnia - Level 2 - Recommended Video
Narnia 2 | Exploiting Stack-Based Buffer Overflow | OverTheWire WargamesПодробнее

Exploitation and Buffer Overflows with Narnia - Level 1Подробнее

Exploitation and Buffer Overflows with Narnia - Level 0Подробнее

Hacking : Narnia@OverTheWire.0rg #0 to #3Подробнее

Solving narnia2 from overthewire - video writeupПодробнее

Narnia 3 | Buffer Overflow via Soft Links | OverTheWire WargamesПодробнее

Binary Exploitation! Buffer Overflow Vulnerability! Narnia4!Подробнее

what ever happened to buffer overflowsПодробнее

Buffer Overflows: A Symphony of ExploitationПодробнее
Introduction to Buffer Overflows (Penetration Testing and Ethical Hacking)Подробнее

3: Return to Win (Ret2Win) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

OverTheWire Narnia 2 WALKTHROUGHПодробнее

Exploiting Simple Buffer Overflows on Win32 : Overwriting The StackПодробнее

Solving narnia3 from overthewire - video writeupПодробнее

Buffer Overflow ExploitПодробнее
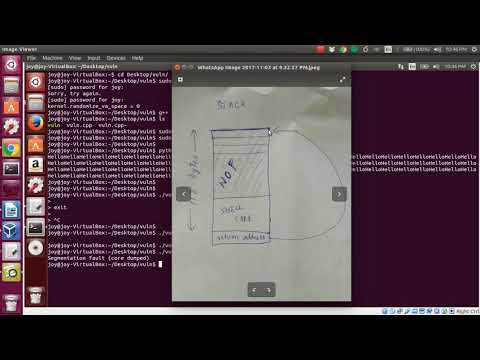
How to exploit a buffer overflow vulnerability - TheoryПодробнее
Exploit Exercises - Fusion - Level 0 (Remote Buffer Overflow Exploit)Подробнее
