Exploit PUT Vulnerability using Poster

sr05 Creating the Department of How Security Awareness that makes your company like you Ira WinklerПодробнее

Exploiting PUT Vulnerability Using NMAPПодробнее

How I exploited a stored image injection vulnerabilityПодробнее

Binary Exploitation vs. Web SecurityПодробнее

Exploiting Efficiency Vulnerabilities in Dynamic Deep Learning Systems- EuroS&P 2025 PostersПодробнее

PUT Method Vuln Find & Exploiting | CadaverПодробнее

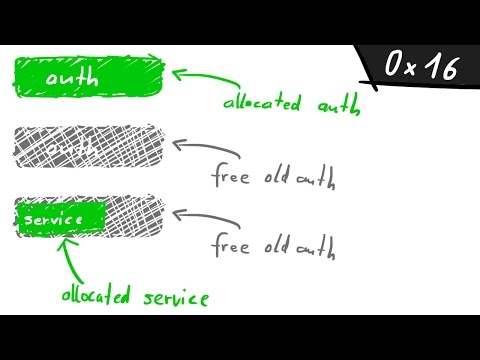
The Heap: How do use-after-free exploits work? - bin 0x16Подробнее
SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Exploiting PUT Method in WebServerПодробнее

Defaced Poc Via HTTP PUT methodПодробнее

Exploiting Time-sensitive VulnerabilitiesПодробнее

Apple Will Pay Hackers $1,000,000 For This Bug Bounty 😳Подробнее

Make Yourself Look Like A Professional HackerПодробнее
Tomcat JSP Upload Bypass via PUT Request - CVE-2017-12617Подробнее

How Attackers Exploit Open Ports! #shorts #shortvideoПодробнее

Exploiting Vulnerabilities Through Proper ReconnaissanceПодробнее

Target of Attack: ClientПодробнее

Live HTML INJECTION Bug hunting POC 👍👍. #bugs #cybersecurity #hacker #hackerone #vulnerabilityПодробнее

Hacking KnowledgeПодробнее

Unmasking Manipulators: Recognizing the Art of Exploiting Vulnerabilities #shorts #shortПодробнее
