dvwa file upload high level using command injections

File Upload | DVWA | Low, Medium & HIGHПодробнее

CARA MELAKUKAN TEKNIK HACKING COMMAND INJECTION | DVWA (low-high security)Подробнее

SQL Injection Security Level Low, Medium, High DVWA Burpsuite Kali LinuxПодробнее

How to Bypass File Upload Restriction using Magic Bytes in DVWA Application Bypass Low, Medium, HighПодробнее
DVWA Pentesting | File Upload |Security Level HighПодробнее

DVWA - Command Injection ( Low, Medium, High, Impossible )Подробнее

DVWA File Upload Vulnerability Walkthrough (Low & Medium)Подробнее
5.2 SQL Injection DVWA Medium and High Difficulty Walkthrough | Web Security for BeginnersПодробнее

DVWA command injection high/medium/low in हिंदी | dvwa tutorials | live bug hunting | hacker vlogПодробнее

Solusi Kerentanan File Upload Di DVWA Level High ( Metasploitable 2 )Подробнее

Cara menghilangkan problem "GD The is not installed" di DVWA linuxПодробнее

File Upload on DVWA Bug Bounty Hunting #hackingПодробнее

DVWA - Kerentanan Pada File Upload ( Low, Medium, High, Impossible )Подробнее

Unrestricted File Upload - How to Exploit Web Servers (With DVWA)Подробнее

DVWA Task 2 – Command ExecutionПодробнее

DVWA COMMAND INJECTION | LOW MEDIUM HIGH | HACKING TUTORIAL | CYBER SECURITY TUTORIAL | HOW TO HACKПодробнее

File Upload | DVWA[Low | Medium | High]Подробнее
![File Upload | DVWA[Low | Medium | High]](https://img.youtube.com/vi/y2q2RsEXp1g/0.jpg)
SQL Injection in DVWA || SQL Injection - Damn Vulnerable Web Application (DVWA)Подробнее
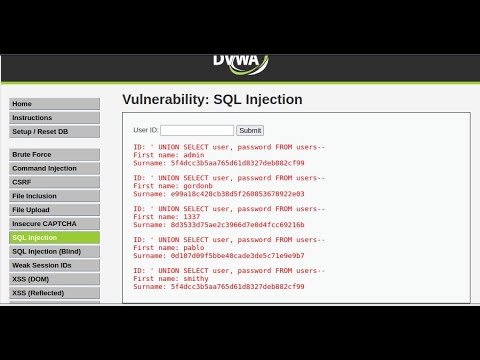
dvwa sql injection high level security 2022Подробнее
