Describe encryption and hashing

Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #securityПодробнее
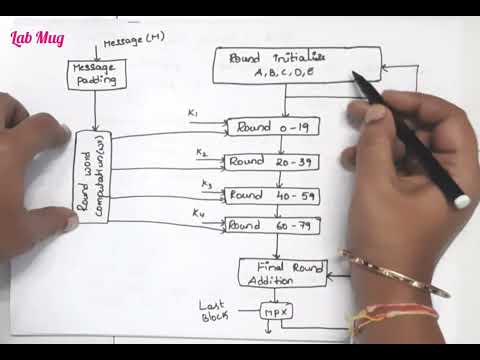
Exchanging Data | 4.1 Compression, Encryption and HashingПодробнее

07) Describe hashing and its application in digital signing.Подробнее

Cryptographic Hash Function (CHF) in Cryptography || Network Security in TeluguПодробнее

MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication CodesПодробнее

SSL TLS Explained: How SSL Certificates & Encryption Keep Your Data Safe [HINDI]Подробнее
![SSL TLS Explained: How SSL Certificates & Encryption Keep Your Data Safe [HINDI]](https://img.youtube.com/vi/I43NnHTeACk/0.jpg)
What is the difference between Encryption and HashingПодробнее

[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256Подробнее
![[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256](https://img.youtube.com/vi/tzB5VD-DzJE/0.jpg)
Encryption Vs Hashing | Difference Between Encryption And Hashing | SimplilearnПодробнее

Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4Подробнее

Birthday Attacks Explained | Brute Force vs. Birthday AttackПодробнее

Hash Functions 🔥🔥Подробнее

Encoding, Encryption and Hashing -- What's the Difference?Подробнее

10 Hashing and Hash Function: Definition, Properties, Hash Pre-image and Hash Collision AttackПодробнее

#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|Подробнее

Encryption - Symmetric Encryption vs Asymmetric Encryption - Cryptography - Practical TLSПодробнее
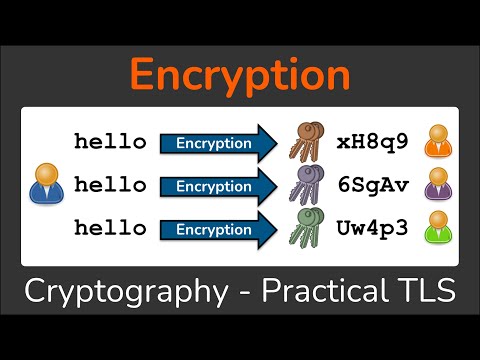
SC-900 EP 07: Encryption, Hashing & SigningПодробнее

MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | SimplilearnПодробнее

What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | SimplilearnПодробнее
