Delphi XE7 Simple Cryptor Source Сode

Delphi XE7 Simple Stealer Source CodeПодробнее

Delphi XE7 Simple Botnet Source CodeПодробнее

Delphi XE7 Encrypt Decrypt Text Symmetric Base64 XEBI XOR Rot13 DESПодробнее

Delphi XE7 TCP Server Client Socket Source CodeПодробнее
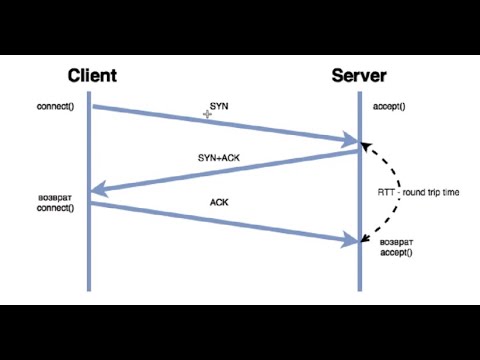
Delphi XE7 Bypass UAC cliconfg.exe and fodhelper.exe Source CodeПодробнее

Update your Delphi source code without any hassleПодробнее

How to protect RAD Studio (Delphi XE & C++) project/Source code filesПодробнее

Delphi - RSA-1024 EncryptionПодробнее

Using Delphi as a No Code Development IDE [On-Demand]Подробнее
![Using Delphi as a No Code Development IDE [On-Demand]](https://img.youtube.com/vi/BR6MSCyERBU/0.jpg)
Parallel Programming Library (Delphi)Подробнее
How ChatGPT can be used to find and fix security issues #cybersecurity #chatgpt #programmingПодробнее

New for Android in Delphi XE7 by Jim McKeethПодробнее

Delphi Static Code Analysis with DerScannerПодробнее

Mobile Delphi apps with TurboCocoa with Vsevolod Leonov - CodeRageXIПодробнее

Location with Delphi XE6Подробнее

Delphi Modernization Made Easy! [On-Demand]Подробнее
![Delphi Modernization Made Easy! [On-Demand]](https://img.youtube.com/vi/JjM_I8HwXcI/0.jpg)
k22 - Cryptor: A New Toolset for Writing Windows Based Self-Encrypting Malware - Jacob MohrbutterПодробнее

AI Poisoning: How Malicious Models Exploit Python Pickle to Bypass SecurityПодробнее
