Decentralized Identity Explained #identitysecurity #iam

#319 - Identity Security & Cyber Resilience with David Mahdi of Transmit SecurityПодробнее

Decentralized Identity Knowledge Limitation #iam #identitysecurityПодробнее

Decentralized identity explainedПодробнее

Decentralized Identity: Benefits for IAM SystemsПодробнее

Identity & Access Management (IAM)Подробнее

Decentralized Identity - ExplainedПодробнее

What is Decentralized Identity?Подробнее

Decentralized Identity is a MustПодробнее

Cybersecurity Architecture: Who Are You? Identity and Access ManagementПодробнее

How Decentralized Identity and Verifiable Claims Disrupt Traditional Identity and Access ManagementПодробнее

Decentralized Identifiers (DIDs) ExplainedПодробнее

What is IAM (Identity and Access Management)?Подробнее
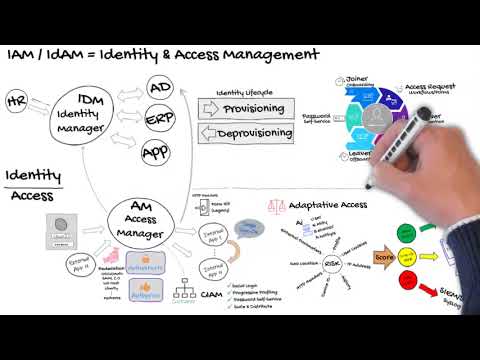
What Is IAM? | Identity and Access Management for Beginners (IAM) | IAM for Beginners | SimplilearnПодробнее

Panel’s Insights on the Future of Identity #identitysecurity #iamПодробнее

Understanding Decentralized IdentityПодробнее

Scaling Identity Security in the Cloud: Automation Strategies for Human and Machine IdentitiesПодробнее

IAM Evolution: Forging a Path to the Idealized Identity Security Matt Caulfield Cisco KeynoteПодробнее

Webinar - The Rise of the Decentralized Identity PlatformПодробнее

iamAlliance: Decentralized IdentityПодробнее

What Is Decentralized Identity? - CryptoBasics360.comПодробнее
