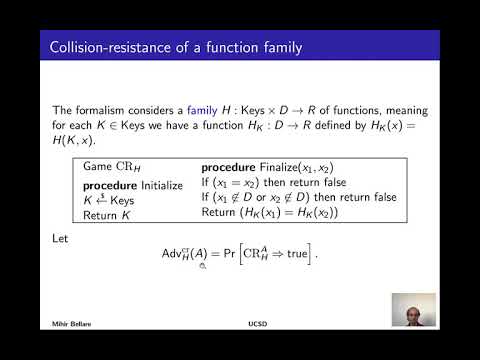
Cryptography on Hardware - Session 9 - Hash Functions, Keccak

Single-Trace Attacks on KeccakПодробнее

Hash Functions explained in detail | Part 11 Cryptography CrashcourseПодробнее

Advanced Cryptography: 3. HashingПодробнее

How to write 12Gh/s Keccak algorithm on VHDL targeting VCU1525Подробнее

SHA: Secure Hashing Algorithm - ComputerphileПодробнее
Portfolio of optimized cryptographic functions based on KeccakПодробнее

Lecture 21 (update): SHA-3 Hash Function by Christof PaarПодробнее

cryptography and network security sha 3 keccak and ripemd 160Подробнее

Encryption vs Encoding vs HashingПодробнее

SHA-3, Keccak and SHAKE (Sponge Function)Подробнее

Fed Up Getting Shattered and Log Jammed? A New Generation of Crypto Is ComingПодробнее

What Are Attacks On Hash Functions? - CryptoBasics360.comПодробнее

What is a Crypto Hash & Why It’s Essential for Blockchain Security?Подробнее

VLSI IMPLEMENTATIONS OF THE CRYPTOGRAPHIC HASH FUNCTIONS MD6Подробнее

Learn Hashing in 1 Minute | What is Hashing | How Hashing Works | Hash Function Explained #shortsПодробнее

What Is The Difference Between SHA And MD5? - SecurityFirstCorp.comПодробнее

Hash FunctionsПодробнее