Computer Security | Buffer Overflow Stack Smashing Detection
Understanding and Dealing with "Stack Smashing Detected" in C++Подробнее

Understanding and Fixing Stack Smashing in C ProgramsПодробнее

Fix The System Detected Overrun Of A Stack - Based Buffer On Windows 10/11Подробнее

Understanding and Dealing with "Stack Smashing Detected" in C++Подробнее

RISC-V Technical Session | Hardware-Based Detection of Stack Buffer Overflow Attacks on RISC-VПодробнее

How Mitigations Work Against Stack-Based Overflows | Free Cyber Security Webinar | CW LabsПодробнее

Understanding and Resolving the "Stack Smashing Detected" ErrorПодробнее

[coding] [c] stack smashing detected hereПодробнее
![[coding] [c] stack smashing detected here](https://img.youtube.com/vi/bI-k3IsJPZQ/0.jpg)
Vulns1001 03 Heap Buffer Overflow CVE-2020-11901💧1️⃣ 01 Background FTFПодробнее

Vulns1001 02 Stack Buffer Overflow CVE-2018-9312🅱️Ⓜ️🅦 01 Background ACID FlowПодробнее

Vulns1001 02 Stack Buffer Overflow CVE-2018-9318🅱️Ⓜ️🅦2️⃣ 01 Background ACID FlowПодробнее

Vulns1001 02 Stack Buffer Overflow 01 IntroПодробнее

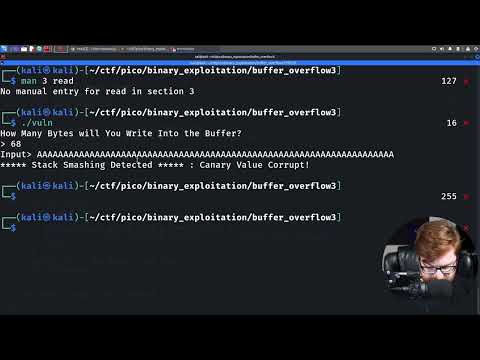
PWN - Bruteforcing Stack Canaries (PicoCTF 2022 #44 'buffer-overflow3')Подробнее
How to exploit a buffer overflow vulnerability (security@cambridge screencast)Подробнее

AN AUTOMATIC DETECTION FOR BUFFER OVERFLOW VULNERABILITIES ON ARM PROCESSORS USING GRAMMAR SETSПодробнее

What is a Buffer Overflow Attack?Подробнее

Buffer Overflow with Checksec and Cyclic | TryHackMe Intro to PWNTOOLSПодробнее

Lecture 3 - Stack smashing attacks, malware, Buffer overflows - Part 2Подробнее

Buffer OverflowПодробнее

Overflows and Stack Smashing Buffer OverflowsПодробнее
