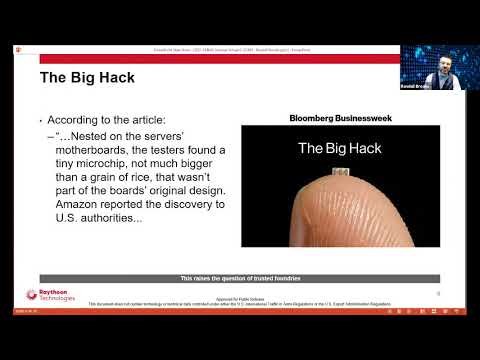
Combating Supply Chain Attacks with Product Security Testing

Hybrid Fortresses: How A Defensible Security Architecture Raises the Bar Against Modern AttacksПодробнее

AI Powered BladeRunners: The Role of AI in Implementing Zero TrustПодробнее

Fortifying Resilience: An In-Depth Exploration of the Overall Product Security Assessment PosterПодробнее
Pushing Cyber Security Forward with Wendi Whitmore | May 2, 2023Подробнее

Preventing Supply Chain Attacks On Open Source Software: Kavitha Venkataswamy & Srinivasan Rangaraj,Подробнее

Cyber Supply Chain Risk Management (SCRM) and its impact on information and Operational TechnologyПодробнее