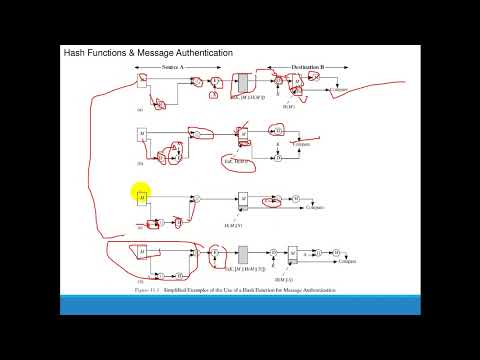
Chapter 11 - Cryptographic Hash Functions
Chapter 11: Hash Tables – Concepts, Functions, Open Addressing | Introduction to Algorithms(Pod Sum)Подробнее

මොනවාද HASH FUNCTION කියන්නේ | Crypto Basic Sinhala Chapter 01 | Part 02Подробнее

Hands-On Security Lab Part 11: Encryption and HashingПодробнее

Cryptography and Network Security lecture 1 Hash function chapter 11Подробнее

Cryptography and Network Security lecture 2 Hash function chapter 11Подробнее

Hash Functions & Digital Signatures | Chapter-5 | Cryptography & Network Security | nesoacademy.orgПодробнее

🔴 FTX CRASH! Sam Bankman-Fried now BANKRUPT - Files Chapter 11 LIVE!Подробнее

11 Chapter 2 The SHA 3 hash functionПодробнее

Part 11: Ethereum cryptographic hash function Keccak 256 (Proof of work vs proof of stake)Подробнее

Ch11 Cryptographic Hash FunctionsПодробнее

Crypto Info Guide Part 2 - Exploiting ComputationПодробнее

CRYPTOGRAPHIC HASH FUNCTIONS in HINDI/URDU | , Secure Hash Algorithm | Birthday Paradox AttackПодробнее

521 chapter 11 part 2Подробнее

Chapter 11 - Cryptographic Hash FunctionsПодробнее

Network security lecture No. 12 By Ms. Sadaf AsadПодробнее

CNS Lec. 10 & 11 Part 2 Iterated Hash function and WhirlpoolПодробнее

HASH FUNCTION || CRYPTOGRAPHY || NETWORK SECURITY PART - 12Подробнее

Cryptographic Hash Functions|Data Security and Encryption in Hindi Urdu CSE348 LECTURE 18Подробнее

Hash Functions explained in detail | Part 11 Cryptography CrashcourseПодробнее
