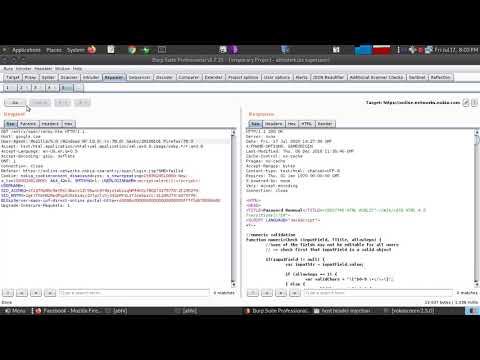
Bug Bounty Hunting SQLI Part 19 | Automation of SQLI Post Based Header Based and Cookie Based

Bug Bounty Hunting SQLI Part 18 | HackersEra | Automation of SQLI GET BasedПодробнее

Bug Bounty Hunting SQLI Part 15 | HackersEra | Exploitation of Cookie Based SQLIПодробнее

Bug Bounty Hunting SQLI Part 11 | HackersEra | Exploitation of POST Based SQLIПодробнее

Bug Bounty Hunting SQLI Part 12 | HackersEra | SQLI Header BasedПодробнее

Bug Bounty Hunting SQLI Part 13 | HackersEra | Exploitation of Header Based SQLIПодробнее

Bug Bounty Hunting SQLI Part 14 | HackersEra | SQLI Cookie BasedПодробнее

Bug Bounty Hunting SQLI Part 3 | HackersEra | Injection Point for SQL InjectionПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Database Breached: The Power of SQL InjectionПодробнее
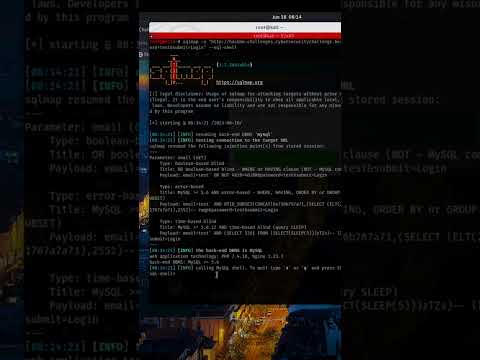
Bug Bounty Hunting SQLI Part 9 | HackersEra | SQLI POST BasedПодробнее

Hacking into the Bank with SQL MapПодробнее
Bug Bounty Hunting SQLI Part 17 | HackersEra | Authentication Bypassing through SQLIПодробнее

SQL Injection POC and True Bug Bounty TutorialsПодробнее

How do companies respond to 0days in 3rd party software?Подробнее

Find SQL Injection vulnerability with sqlmapПодробнее
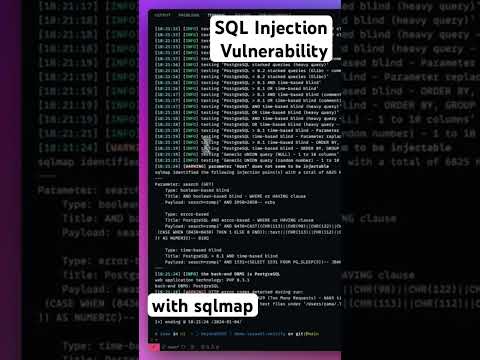
$30,000 blind SQL injection chained with blind XSS #bugbounty #bugbountytips #bugbountyhunterПодробнее

Host Header Injection Vulnerability | POC | Bug Bounty 2020Подробнее