Buffer Overflow - Shellcode + Stack leak address

Making stack executable with malicious mprotect call - pwn110 - PWN101 | TryHackMeПодробнее

How to Bypass Canary, PIE, NX Protection Utilizing Format String VulnerabilityПодробнее

Monitoring Surveillance Vendors: A Deep Dive into In-the-Wild Android Full Chains in 2021Подробнее

Shellcode Execution (ret2shellcode) - pwn104 - PWN101 | TryHackMeПодробнее

10: Bypassing Stack Canaries (leak + write) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

8: Leak PIE (bypass) and Lib-C (ret2system) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

7: Format String Vulnerabilities (printf) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Bypassing Stack Canaries and NX/DEP (Ret2Lib-C) - Bird - [Intigriti 1337UP LIVE CTF 2022]Подробнее
![Bypassing Stack Canaries and NX/DEP (Ret2Lib-C) - Bird - [Intigriti 1337UP LIVE CTF 2022]](https://img.youtube.com/vi/XaWlKYgmEDs/0.jpg)
Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]Подробнее
![Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]](https://img.youtube.com/vi/jU7yB-elFV8/0.jpg)
Buffer Overflow with Shellcode Injection - Easy Register - [Intigriti 1337UP LIVE CTF 2022]Подробнее
![Buffer Overflow with Shellcode Injection - Easy Register - [Intigriti 1337UP LIVE CTF 2022]](https://img.youtube.com/vi/790lGRdyXaE/0.jpg)
Introduction to memory exploitation - Patricia Aas - Meeting C++ 2021Подробнее

Hack The Box - Introduction to Binary Exploitation - PwnShop - Stack Pivot, Ret2LIBC [Walkthrough]Подробнее
![Hack The Box - Introduction to Binary Exploitation - PwnShop - Stack Pivot, Ret2LIBC [Walkthrough]](https://img.youtube.com/vi/i_5VQF18suQ/0.jpg)
x64 Linux Binary Exploitation TrainingПодробнее
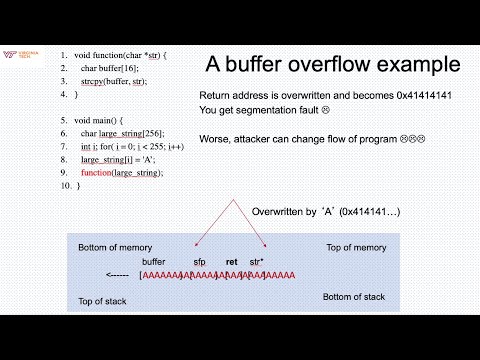
Lecture September 15 2020 Stack buffer overflow attackПодробнее
CPPP 2019 - The Anatomy of an Exploit - Patricia AasПодробнее

Exploiting Buffer Overflows on RISC-V - Christina Quast, NoneПодробнее

DEF CON 26 - zerosum0x0 - Demystifying MS17 010 Reverse Engineering the ETERNAL ExploitsПодробнее
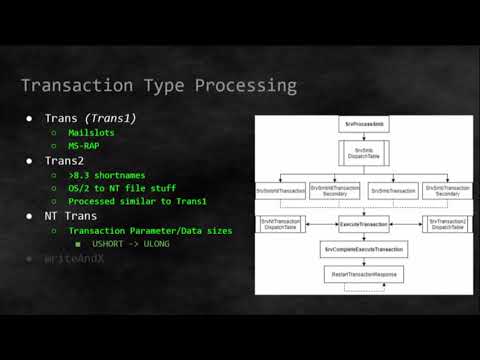
BlueBorne - A New Class of Airborne Attacks that can Remotely Compromise Any Linux/IoT DeviceПодробнее

How to Bypass ASLR using an Information Leak (for Stack Overflow Exploit)Подробнее
