Buffer Overflow Attacks Explained #cybersecurity #bufferoverflow #ethicalhacking #itsecurity

Buffer Overflow? Not Today! 🚫Подробнее

Атака переполнения буфера, объясненная в кибербезопасностиПодробнее
Buffer Overflow Explained With PracticalПодробнее

What Is BUFFER OVERFLOW? | Overflow Of Input | Programming Errors ExplainedПодробнее

Buffer OverflowПодробнее

What is a Buffer Overflow Attack?Подробнее

What is buffer overflow?Подробнее
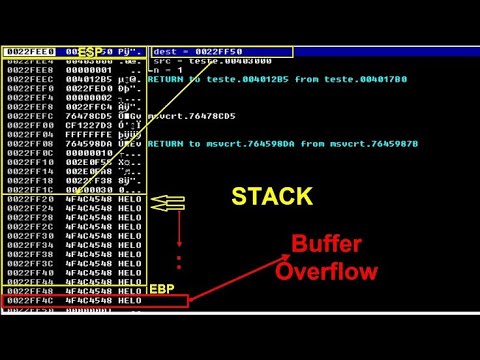
Understanding Buffer Overflow: A Key Cybersecurity Vulnerability | Explained Under 60 SecondsПодробнее

Buffer Overflow Attacks Explained | How Hackers Exploit Memory?Подробнее

What Is Buffer Overflow? Attacks and Risks ExplainedПодробнее

Binary Exploitation vs. Web SecurityПодробнее

What is Buffer Overflow Attack ? #cyberattack #shortsПодробнее

What are Buffer overflow, race condition, error handling, and improper input attacks.Подробнее
Buffer Overflows - CompTIA Security+ SY0-701 - 2.3Подробнее

Ethical Hacking - Uses of Buffer Overflow Attacks in Ethical HackingПодробнее

Buffer Overflow Explained with Live Demo | The Silent System Killer (Beginner-Friendly)Подробнее

Buffer Overflow Attacks Explained with Examples ComparitechПодробнее

Cyber Security| Unit: 3| BCC301/BCC 401/ BCC401H Buffer Overflow in Cyber Security|#BufferOverflowПодробнее

Ethical Hacking - Examples of Buffer Overflow AttacksПодробнее

Cyber security training in Hindi class-54 || What is buffer overflow in Hindi?Подробнее

CompTIA Security+ (SY0-701) Question: Buffer Overflow VulnerabilityПодробнее
Buffer overflow exploits explained with beer! [Cyber Security Education]Подробнее
![Buffer overflow exploits explained with beer! [Cyber Security Education]](https://img.youtube.com/vi/7LDdd90aq5Y/0.jpg)
What Is BUFFER OVERFLOW? | Overflow Of InputПодробнее
