Binary Exploitation - CSE365 - Connor - 2024.11.20

Binary Exploitation vs. Web SecurityПодробнее

Is Binary Exploitation STILL Worth Learning Today? #security #hacking #binaryexploitationПодробнее

Binary Exploitation - CSE365 - Yan - 2024.11.25Подробнее

Binary Exploitation - CSE365 - Muhilan 2024.04.23Подробнее

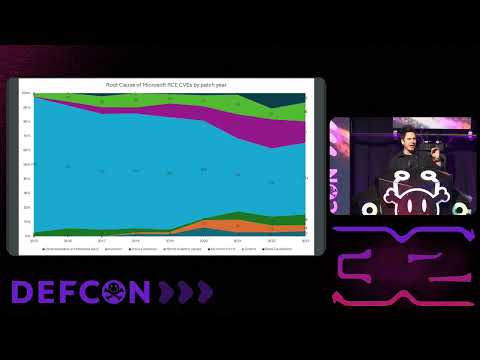
DEF CON 32 - The Rise and Fall of Binary Exploitation - Stephen SimsПодробнее
Binary Exploitation - CSE365 - Connor - 2024.04.30Подробнее

What modern binary exploitation looks likeПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

💻 Unveiling the Ultimate Privilege Escalation Hack Unraveling VulnerabilitiesПодробнее

Binary Exploitation - CSE365 - Connor - 2024.04.22Подробнее

Critical NetScaler Vulnerabilities CVE-2025-5777 "CitrixBleed 2" and CVE-2025-6543 Exploited WildПодробнее

🤖 Binary Exploitation x Web Security #BinaryExploitation #websecurity #portswigger #sandbox #hackingПодробнее
