Binary Encryption Demo

Why BINARY REWRITING is the FUTURE of ObfuscationПодробнее

Encoding Encryption Hashing | Web and Data security & integrity essentialsПодробнее

Understand the difference between encryption, hashing, and encoding easilyПодробнее

Can you decrypt a hashed password? #shorts #encryption #hashing #passwordПодробнее

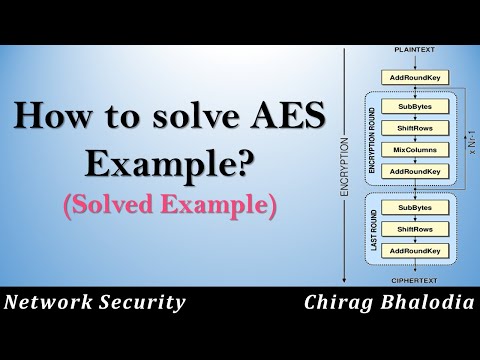
How to solve AES example? | AES Encryption Example | AES solved Example | AES Example solutionПодробнее
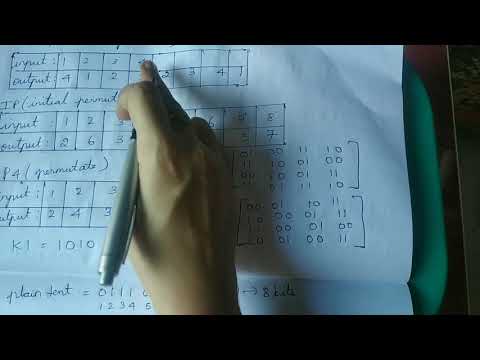
Simplified DES(Data Encryption Standard)(Information Security)Подробнее
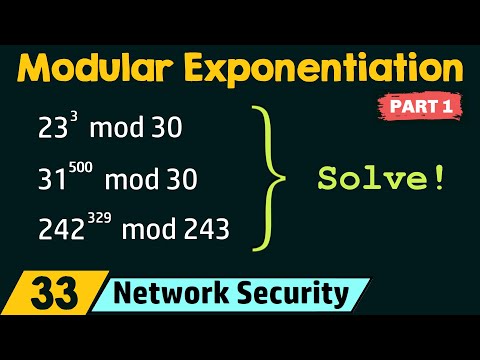
Modular Exponentiation (Part 1)Подробнее
CISSP Exam Cram - Cryptography Drill-DownПодробнее

AES IV - Advanced Encryption Standard - Encryption and Decryption - Cyber Security CSE4003Подробнее
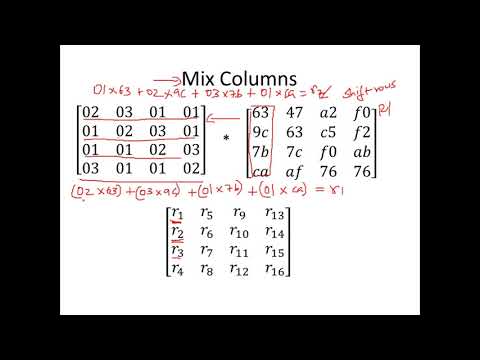
AES I - Group, Ring, Field and Finite Field - Abstract Algebra Basics - Cyber Security - CSE4003Подробнее

DES Numerical Illustration | Network SecurityПодробнее
January 2020 BPatch Encryption DemoПодробнее

7. Adaptive Huffman Coding | ENCODING example | Adaptive Huffman Encryption and DecryptionПодробнее

Lec-81: Symmetric Key Cryptography in Network Security with examplesПодробнее
AWS KMS - Encrypt & Decrypt DEMO | KMS pricing | KMS Key Rotation (Part 2)Подробнее

Fully Homomorphic EncryptionПодробнее
