Asset Threat and Risk Management
persentasi operationally critical threat, asset, and vulnerability evaluation (OCTAVE)Подробнее

Top secrets for asset recognition and threat evaluationПодробнее

Protect Your Assets: The Rising Threat of Data Breaches #financialfreedom #financialsmartnessПодробнее

Mastering Asset Identification and Threat Assessment #healthcare #cybersecurity #risk #healthПодробнее

Understanding Threats, Risks, and Vulnerabilities for CC & Security+ SuccessПодробнее

Strategies for Cloud Security Risk Management | Google Cloud Cybersecurity CertificateПодробнее

Cybersecurity risk identification process, asset, threat, vulnerability, internal & external threatsПодробнее

Master Practical Risk Assessment Techniques : Step-by-Step Guide 2024Подробнее

ISO 27001:2022 Lead Implementer Series #2 Mastering Risk Assessment with ChatGPT:Подробнее

Risk Management MindMap (3 of 3) | CISSP Domain 1Подробнее

Estimating Risk for Threat Asset PairsПодробнее

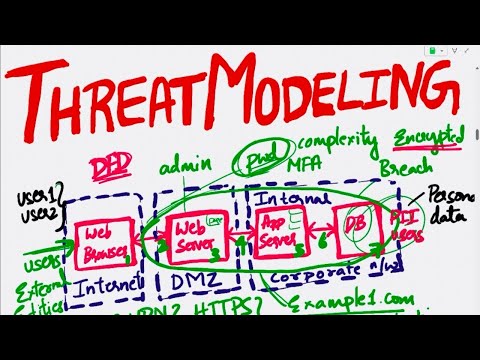
Threat Modeling Explained| How to implement threat modeling| Pros and Cons of Threat Modeling MethodПодробнее
How to Perform Effective OT Cyber Security Risk AssessmentsПодробнее

Securing Your Digital Assets: A Step-by-Step Guide to Cybersecurity Threat and Risk Assessment (TRA)Подробнее

Cybersecurity Assets, Network Threats & Vulnerabilities | Google Cybersecurity CertificateПодробнее

How To Manage Security Risks & Threats | Google Cybersecurity CertificateПодробнее
#TrendingTuesdays S2 EO2: Risk Insights - Know Your Attack SurfaceПодробнее

Threat Modeling Frameworks for Information Security Analysts | Threats and Attack VectorsПодробнее

"Unlock the Secret to Building the Perfect Risk Management Plan"Подробнее
Risk Assessment and ManagementПодробнее
