A Unified Approach to Role Based Access Control

A Unified Approach to Tackle Export Controls, NIST 800-171 (CUI), and CMMCПодробнее

A Unified Approach to Clouds, Containers, and PaaS Services with Morpheus DataПодробнее

Z-Nights 2021, February - Cloud Native Serverless Access Control, Peter VerhasПодробнее

Role-based access control (RBAC) vs. Attribute-based access control (ABAC)Подробнее

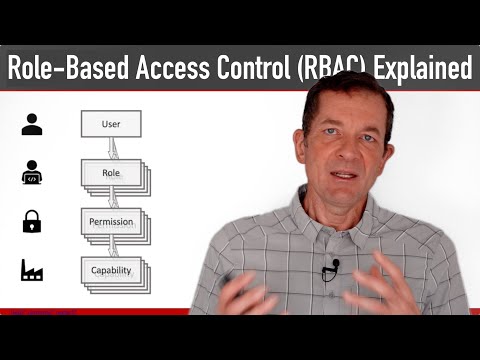
Role-Based Access Control (RBAC) Explained: How it works and when to use itПодробнее
Role-based access control (RBAC) in Microsoft Defender for EndpointПодробнее

Mastering RBAC: A Simplified Guide to Role-Based Access ControlПодробнее

Role-based access control (RBAC)Подробнее

Who's Allowed to Do What? RBAC vs. ABAC & The Art of Access ControlПодробнее

Role-based access control (RBAC) in Microsoft Defender ATPПодробнее

Enhancing Workplace Safety and Security Conceptualising the Role of Crime Prevention Clubs in MalaysПодробнее

Understand Role Based Access Control in KubernetesПодробнее
Microsoft Entra ID | Role-based access control for applications - Part 1Подробнее

Role-based access control (RBAC)Подробнее

Microsoft 365 Defender: Unified RBACПодробнее

Role based access controlПодробнее

What is Attribute Based Access Control (ABAC) - IAMПодробнее

RBAC: Not a Setting, A Strategy! #shortsПодробнее

Attribute Based Access Control ABACПодробнее

What is Role Based Access Control (RBAC)?Подробнее

What is PBAC? Policy Based Access Control Explainer by PlainIDПодробнее
