3 Ways How Attackers Can Reverse Engineer Your Android App (+ How You Protect It!)

Reverse Engineer an Android Application | Hac an Android Phone with Armitage | Ethical HackingПодробнее

Securing the System: A Deep Dive into Reversing Android Pre-Installed AppsПодробнее

DEF CON 26 - Krotofil , Wetzels - Thru the Eyes of the Attacker Designing Embedded Systems for ICSПодробнее

34C3 - Inside Android’s SafetyNet Attestation: Attack and DefenseПодробнее

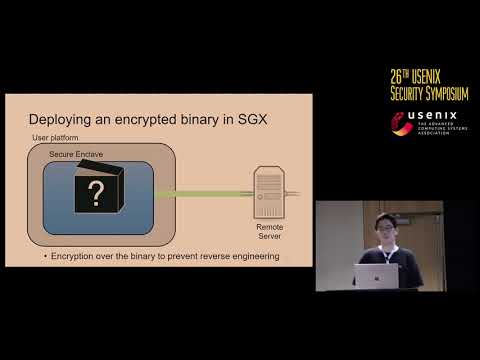
USENIX Security '17 - Hacking in Darkness: Return-oriented Programming against Secure EnclavesПодробнее
Reverse Engineering Android Applications - Tom KeetchПодробнее

30C3: Hardware Attacks, Advanced ARM Exploitation, and Android Hacking (EN)Подробнее

SCS3: Julien Bachmann - iOS Applications Reverse EngineeringПодробнее
