1.3 Hash Functions - Cryptography by Andrew @PBA4

Exercise 1: Hash functionsПодробнее

Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003Подробнее
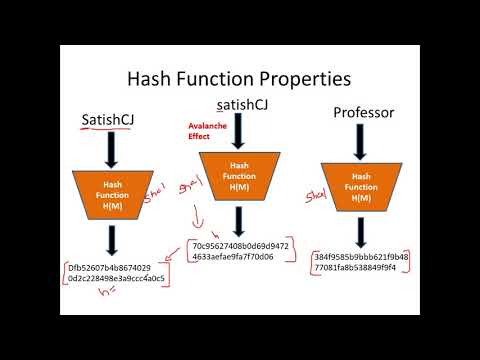
11 Cryptographic Hash Function and its Properties: Pre-image, Second Pre-image, Collision ResistanceПодробнее

21. Cryptography: Hash FunctionsПодробнее

[CompNetSec] - 13 - Cryptographic Hash FunctionsПодробнее
![[CompNetSec] - 13 - Cryptographic Hash Functions](https://img.youtube.com/vi/2yxHePuitJc/0.jpg)
6.875 (Cryptography) L17: Hash Functions, Random OraclesПодробнее

Lecture 21 (update): SHA-3 Hash Function by Christof PaarПодробнее

Cryptographic Hash Functions (Part 1): OverviewПодробнее

Cryptographic Hash Function Solution - Applied CryptographyПодробнее

Cryptographic Hash Functions (CO4: Session-1)Подробнее

Cryptography and Network Security lecture 1 Hash function chapter 11Подробнее

SHA: Secure Hashing Algorithm - ComputerphileПодробнее
One Way Hash ExplainedПодробнее

Can you decrypt a hashed password? #shorts #encryption #hashing #passwordПодробнее

Hashing Algorithms and Security - ComputerphileПодробнее
Hashing and Hashing Algorithms - md5 sha1 sha256 sha2 sha3 - Cryptography EssentialsПодробнее
NSC 3 3 1 Hash Functions in Public key cryptographyПодробнее

CSE571-11-11: Cryptographic Hash FunctionsПодробнее

Hash Functions Explained in 60 Seconds! #learnandgrow #technology #blockchain #shorts #automationПодробнее
