🛠️ Windows Virtual Memory Explained 📚 Windows Internals 💻
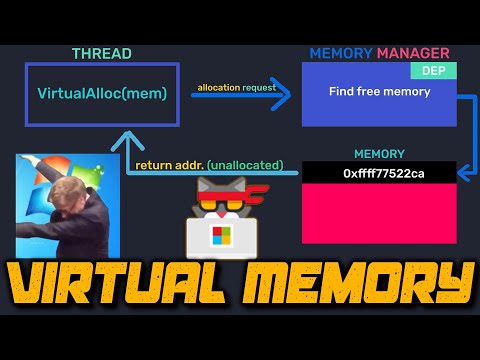
SOC Lvl. 2 | EP.40 | Windows Internals | TryHackMe Malware AnalysisПодробнее

What is Disk Paging? Virtual Memory Explained!Подробнее

Windows Internals - Part 2Подробнее

Understainding Windows OS Processes and Internals | TryHackMe InternalsПодробнее

But, what is Virtual Memory?Подробнее
Windows Internals Crash CourseПодробнее
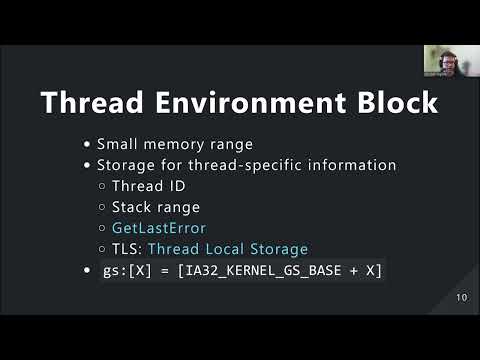
Windows Internals - Special Process Types ExplainedПодробнее
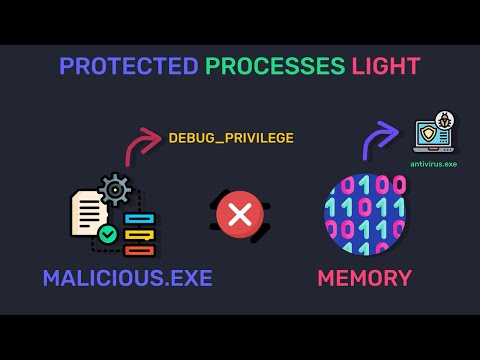
Windows Internals - Processes and Threads ExplainedПодробнее
Windows Internals for Red TeamsПодробнее
Windows Internals: Walking the Process Environment Block to Discover In-Memory LibrariesПодробнее
Windows Internals [Red Team Training] -- TryHackMe LIVE!Подробнее
![Windows Internals [Red Team Training] -- TryHackMe LIVE!](https://img.youtube.com/vi/k7UDasbkLJw/0.jpg)
Abusing Windows Internals - Part Three | Alternate Memory Execution TechniquesПодробнее

Abusing Windows Internals - Part One | ShellCode Injection | Process HollowingПодробнее

Underlying Components of Windows | Processes | Threads | DLLs | PE File //Perumal JeganПодробнее

Windows Offender: Reverse Engineering Windows Defender's Antivirus EmulatorПодробнее

Windows Internals - Processes Part 19 of 20, Address Space and security internalsПодробнее

Windows Internals - Processes Part 9 of 20 - Assets of the process - Address Space.Подробнее

Windows Internals - Processes Part 4 of 20 - Understanding the concept of a process in windows.Подробнее

Windows Internals - Processes Part 2 of 20 - Introduction to process in windows.Подробнее
